Friday, July 31, 2009
Monday, July 27, 2009
History of java
For the past 13 years, Java has changed our world . . . and our expectations..
Today, with technology such a part of our daily lives, we take it for granted that we can be connected and access applications and content anywhere, anytime. Because of Java, we expect digital devices to be smarter, more functional, and way more entertaining.
In the early 90s, extending the power of network computing to the activities of everyday life was a radical vision. In 1991, a small group of Sun engineers called the "Green Team" believed that the next wave in computing was the union of digital consumer devices and computers. Led by James Gosling, the team worked around the clock and created the programming language that would revolutionize our world – Java.
The Green Team demonstrated their new language with an interactive, handheld home-entertainment controller that was originally targeted at the digital cable television industry. Unfortunately, the concept was much too advanced for the them at the time. But it was just right for the Internet, which was just starting to take off. In 1995, the team announced that the Netscape Navigator Internet browser would incorporate Java technology.
Today, Java not only permeates the Internet, but also is the invisible force behind many of the applications and devises that power our day-to-day lives. From mobile phones to handheld devises, games and navigation systems to e-business solutions, Java is everywhere!
Wednesday, July 15, 2009
Performance Test for Java While loop, For loop and Iterator
Do you wonder which of the following methods are the faster way to loop through a list or collection before?
1) While Loop
2) For Loop
3) Iterator Loop
Performance Test – While , For and Iterator
Here i create a simple program to loop through a List with 1,5,10 and 15 millions of data in While loop, For loop and Iterator loop. It’s will calculate and display the elapsed time in output.
Here is the performance test source code
public class ArrayToList {
public static void main(String[] argv) {
String sArray[] = createArray();
//convert array to list
List lList = Arrays.asList(sArray);
System.out.println("\n--------- Iterator Loop -------\n");
long lIteratorStartTime = new Date().getTime();
System.out.println("Start: " + lIteratorStartTime);
//iterator loop
Iterator
while ( iterator.hasNext() ){
String stemp = iterator.next();
}
long lIteratorEndTime = new Date().getTime();
System.out.println("End: " + lIteratorEndTime);
long lIteratorDifference = lIteratorEndTime - lIteratorStartTime;
System.out.println("Iterator - Elapsed time in milliseconds: " + lIteratorDifference);
System.out.println("\n-------END-------");
System.out.println("\n--------- For Loop --------\n");
long lForStartTime = new Date().getTime();
System.out.println("Start: " + lForStartTime);
//for loop
for (int i=0; i<>
String stemp = (String)lList.get(i);
}
long lForEndTime = new Date().getTime();
System.out.println("End: " + lForEndTime);
long lForDifference = lForEndTime - lForStartTime;
System.out.println("For - Elapsed time in milliseconds: " + lForDifference);
System.out.println("\n-------END-------");
System.out.println("\n--------- While Loop -------\n");
long lWhileStartTime = new Date().getTime();
System.out.println("Start: " + lWhileStartTime);
//while loop
int j=0;
while (j<>
{
String stemp = (String)lList.get(j);
j++;
}
long lWhileEndTime = new Date().getTime();
System.out.println("End: " + lWhileEndTime);
long lWhileDifference = lWhileEndTime - lWhileStartTime;
System.out.println("While - Elapsed time in milliseconds: " + lWhileDifference);
System.out.println("\n-------END-------");
}
static String [] createArray(){
String sArray[] = new String [15000000];
for(int i=0; i<15000000;>
sArray[i] = "Array " + i;
return sArray;
}
}
Output
D:\test>java -Xms1024m -Xmx1024m ArrayToList
--------- Iterator Loop -------
Start: 1232435614372
End: 1232435614763
Iterator - Elapsed time in milliseconds: 390
-------END-------
--------- For Loop --------
Start: 1232435614763
End: 1232435614997
For - Elapsed time in milliseconds: 234
-------END-------
--------- While Loop -------
Start: 1232435614997
End: 1232435615232
While - Elapsed time in milliseconds: 234
-------END-------
Performance Test Result (in milliseconds)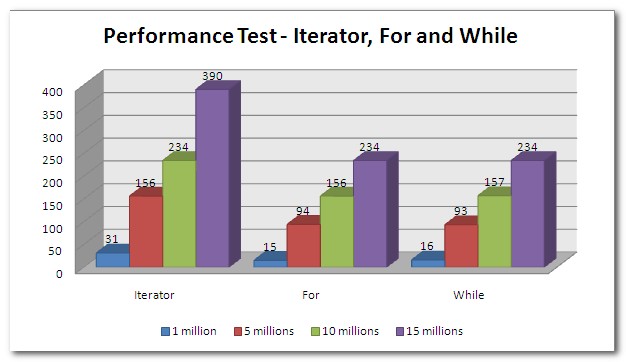
Conclusion
Well… the result show Iterator mechanism is the slowest method to loop through a list. There’s not much performance different between For and While loop.
Iterator provides a very handy way to loop through a list or collection, but it is slower than For and While loop. Please be remind that the different is just in milliseconds (not even 1 second for 15 millions of data looping). So, just choose any looping mechanism you want, there’s not much performance different.
Monday, July 13, 2009
Software Protection Solutions
Software protection is need of the day. It is estimated that about 30% revenue is lost due to piracy but these figures fail to explain the fact that piracy also increases legal sales. Director of a software company told me they learn about some companies using their pirated software but they did not took any action. The director was not surprised when he received order from the same company next year. He said in the absence of a workable demo or just to try full features before making a purchase decision many people use pirated versions. This does not mean that software companies should not protect their products but only mean that a legal demonstrable product should be made available to customer for evaluation for a sufficient period of time.
Saturday, July 11, 2009
How to make your IE be fast like other browsers?
Reasons for computer crash and tips to prevent
Listing few reasons for your computer crash or hangs, and the steps for how to rectify it.
1) Hardware conflict
The number one reason why Windows crashes is hardware conflict. Each hardware device communicates to other devices through an interrupt request channel (IRQ). These are supposed to be unique for each device.
For example, a printer usually connects internally on IRQ 7. The keyboard usually uses IRQ 1 and the floppy disk drive IRQ 6. Each device will try to hog a single IRQ for itself.
If there are a lot of devices, or if they are not installed properly, two of them may end up sharing the same IRQ number. When the user tries to use both devices at the same time, a crash can happen. The way to check if your computer has a hardware conflict is through the following route:
* Start-Settings-Control Panel-System-Device Manager.
Often if a device has a problem a yellow '!' appears next to its description in the Device Manager. Highlight Computer (in the Device Manager) and press Properties to see the IRQ numbers used by your computer. If the IRQ number appears twice, two devices may be using it.
Sometimes a device might share an IRQ with something described as 'IRQ holder for PCI steering'. This can be ignored. The best way to fix this problem is to remove the problem device and reinstall it.
When working inside a computer you should switch it off, unplug the mains lead and touch an unpainted metal surface to discharge any static electricity.
To be fair to Mcft, the problem with IRQ numbers is not of its making. It is a legacy problem going back to the first PC designs using the IBM 8086 chip. Initially there were only eight IRQs. Today there are 16 IRQs in a PC. It is easy to run out of them. There are plans to increase the number of IRQs in future designs.
2) Bad Ram
Ram (random-access memory) problems might bring on the blue screen of death with a message saying Fatal Exception Error. A fatal error indicates a serious hardware problem. Sometimes it may mean a part is damaged and will need replacing.
But a fatal error caused by Ram might be caused by a mismatch of chips. For example, mixing 70-nanosecond (70ns) Ram with 60ns Ram will usually force the computer to run all the Ram at the slower speed. This will often crash the machine if the Ram is overworked.
One way around this problem is to enter the BIOS settings and increase the wait state of the Ram. This can make it more stable. Another way to troubleshoot a suspected Ram problem is to rearrange the Ram chips on the motherboard, or take some of them out. Then try to repeat the circumstances that caused the crash. When handling Ram try not to touch the gold connections, as they can be easily damaged.
Parity error messages also refer to Ram. Modern Ram chips are either parity (ECC) or non parity (non-ECC). It is best not to mix the two types, as this can be a cause of trouble.
EMM386 error messages refer to memory problems but may not be connected to bad Ram. This may be due to free memory problems often linked to old Dos-based programmes.
3) BIOS settings
Every motherboard is supplied with a range of chipset settings that are decided in the factory. A common way to access these settings is to press the F2 or delete button during the first few seconds of a boot-up.
Once inside the BIOS, great care should be taken. It is a good idea to write down on a piece of paper all the settings that appear on the screen. That way, if you change something and the computer becomes more unstable, you will know what settings to revert to.
A common BIOS error concerns the CAS latency. This refers to the Ram. Older EDO (extended data out) Ram has a CAS latency of 3. Newer SDRam has a CAS latency of 2. Setting the wrong figure can cause the Ram to lock up and freeze the computer's display.
Mcft Windows is better at allocating IRQ numbers than any BIOS. If possible set the IRQ numbers to Auto in the BIOS. This will allow Windows to allocate the IRQ numbers (make sure the BIOS setting for Plug and Play OS is switched to 'yes' to allow Windows to do this.).
4) Hard disk drives
After a few weeks, the information on a hard disk drive starts to become piecemeal or fragmented. It is a good idea to defragment the hard disk every week or so, to prevent the disk from causing a screen freeze. Go to
* Start-Programs-Accessories-System Tools-Disk Defragmenter
This will start the procedure. You will be unable to write data to the hard drive (to save it) while the disk is defragmenting, so it is a good idea to schedule the procedure for a period of inactivity using the Task Scheduler.
The Task Scheduler should be one of the small icons on the bottom right of the Windows opening page (the desktop).
Some lockups and screen freezes caused by hard disk problems can be solved by reducing the read-ahead optimisation. This can be adjusted by going to
* Start-Settings-Control Panel-System Icon-Performance-File System-Hard Disk.
Hard disks will slow down and crash if they are too full. Do some housekeeping on your hard drive every few months and free some space on it. Open the Windows folder on the C drive and find the Temporary Internet Files folder. Deleting the contents (not the folder) can free a lot of space.
Empty the Recycle Bin every week to free more space. Hard disk drives should be scanned every week for errors or bad sectors. Go to
* Start-Programs-Accessories-System Tools-ScanDisk
Otherwise assign the Task Scheduler to perform this operation at night when the computer is not in use.
5) Fatal OE exceptions and VXD errors
Fatal OE exception errors and VXD errors are often caused by video card problems.
These can often be resolved easily by reducing the resolution of the video display. Go to
* Start-Settings-Control Panel-Display-Settings
Here you should slide the screen area bar to the left. Take a look at the colour settings on the left of that window. For most desktops, high colour 16-bit depth is adequate.
If the screen freezes or you experience system lockups it might be due to the video card. Make sure it does not have a hardware conflict. Go to
* Start-Settings-Control Panel-System-Device Manager
Here, select the + beside Display Adapter. A line of text describing your video card should appear. Select it (make it blue) and press properties. Then select Resources and select each line in the window. Look for a message that says No Conflicts.
If you have video card hardware conflict, you will see it here. Be careful at this point and make a note of everything you do in case you make things worse.
The way to resolve a hardware conflict is to uncheck the Use Automatic Settings box and hit the Change Settings button. You are searching for a setting that will display a No Conflicts message.
Another useful way to resolve video problems is to go to
* Start-Settings-Control Panel-System-Performance-Graphics
Here you should move the Hardware Acceleration slider to the left. As ever, the most common cause of problems relating to graphics cards is old or faulty drivers (a driver is a small piece of software used by a computer to communicate with a device).
Look up your video card's manufacturer on the internet and search for the most recent drivers for it.
6) Viruses
Often the first sign of a virus infection is instability. Some viruses erase the boot sector of a hard drive, making it impossible to start. This is why it is a good idea to create a Windows start-up disk. Go to
* Start-Settings-Control Panel-Add/Remove Programs
Here, look for the Start Up Disk tab. Virus protection requires constant vigilance.
A virus scanner requires a list of virus signatures in order to be able to identify viruses. These signatures are stored in a DAT file. DAT files should be updated weekly from the web-site of your antivirus software manufacturer.
7) Printers
The action of sending a document to print creates a bigger file, often called a postscript file.
Printers have only a small amount of memory, called a buffer. This can be easily overloaded. Printing a document also uses a considerable amount of CPU power. This will also slow down the computer's performance.
If the printer is trying to print unusual characters, these might not be recognised, and can crash the computer. Sometimes printers will not recover from a crash because of confusion in the buffer. A good way to clear the buffer is to unplug the printer for ten seconds. Booting up from a powerless state, also called a cold boot, will restore the printer's default settings and you may be able to carry on.
8) Software
A common cause of computer crash is faulty or badly-installed software. Often the problem can be cured by uninstalling the software and then reinstalling it. Use Norton Uninstall or Uninstall Shield to remove an application from your system properly. This will also remove references to the programme in the System Registry and leaves the way clear for a completely fresh copy.
The System Registry can be corrupted by old references to obsolete software that you thought was uninstalled. Use Reg Cleaner by Jouni Vuorio to clean up the System Registry and remove obsolete entries. It works on Windows 95, Windows 98, Windows 98 SE (Second Edition), Windows Millennium Edition (ME), NT4 and Windows 2000 , Windows Xp.
Often a Windows problem can be resolved by entering Safe Mode. This can be done during start-up. When you see the message "Starting Windows" press F4. This should take you into Safe Mode.
Safe Mode loads a minimum of drivers. It allows you to find and fix problems that prevent Windows from loading properly.
Sometimes installing Windows is difficult because of unsuitable BIOS settings. If you keep getting SUWIN error messages (Windows setup) during the Windows installation, then try entering the BIOS and disabling the CPU internal cache. Try to disable the Level 2 (L2) cache if that doesn't work.
Remember to restore all the BIOS settings back to their former settings following installation.
9) Overheating
Central processing units (CPUs) are usually equipped with fans to keep them cool. If the fan fails or if the CPU gets old it may start to overheat and generate a particular kind of error called a kernel error. This is a common problem in chips that have been overclocked to operate at higher speeds than they are supposed to.
CPU problems can often be fixed by disabling the CPU internal cache in the BIOS. This will make the machine run more slowly, but it should also be more stable.
10) Power supply problems
With all the new construction going on around the country the steady supply of electricity has become disrupted. A power surge or spike can crash a computer as easily as a power cut.
If this has become a nuisance for you then consider buying a uninterrupted power supply (UPS). This will give you a clean power supply when there is electricity, and it will give you a few minutes to perform a controlled shutdown in case of a power cut.
It is a good investment if your data are critical, because a power cut will cause any unsaved data to be lost.
Note: There can also be many reasons exept these so don’t rely on these totally
Wednesday, July 8, 2009
How a denial-of-service attack works
How does this type of cyber attack work? And how can people make sure their computers are safe?
Here are some questions and answers about the attack.
Q: What is a "denial-of-service" attack?
A: Think about what would happen if you and all your friends called the same restaurant over and over and ordered things you didn't even really want. You'd jam the phone lines and overwhelm the kitchen to the point that it couldn't take any more new orders.
That's what happens to Web sites when criminals hit them withdenial-of-service attacks. They're knocked offline by too many junk requests from computers controlled by the attackers.
The bad guys' main weapons in such an attack are "botnets," or networks of "zombie" personal computers they've infected with a virus. The virus lets the criminals remotely control innocent people's machines, which are programmed to contact certain Web sites over and over until that overwhelms the servers that host the sites. The servers become too busy to respond to anything, and the Web site slows or stops working altogether.
It's different from what usually happens when you try to access a Web site. Normally, you just make one request to see the site, and unless there's a crush of traffic from something like a big news event, the servers respond well. Hijacked PCs, on the other hand, are programmed to send way more traffic than a normal user could generate on his or her own.
Q: How often do these attacks happen?
A: People try denial-of-service attacks all the time — many government and private sites report being hit every day. Often the assaults are unsuccessful, because Web sites have ways of identifying and intercepting malicious traffic. However, sites really want to avoid blocking legitimate Web users, so more often than not, Internet traffic is let through until a problem is spotted.
Denial-of-service attacks are noisy by design, and they intend to make a statement. They're not subtle attempts to infiltrate a Web site's defenses, which can be much more insidious because that gives hackers access to whatever confidential information is stored there.
Often the attacks take a site out for a few hours, before Web site administrators can respond. What made the most recent attack notable is that it was widespread and went on for a while, beginning over the July Fourth holiday weekend and running into this week. It's not yet clear how the attack was able to last that long.
Q: Some organizations appear to have fended off these recent attacks, while other Web sites went down. How can this be?
A: The sites that went down probably were less prepared, because they are less accustomed to being hit or aren't sensitive enough to warrant extra precautions.
Popular Web sites, like e-commerce and banking sites, have a lot of experience dealing with denial-of-service attacks, and they have sophisticated software designed to identify malicious traffic. Often that's done by flagging suspicious traffic flowing into the site, and if there's enough of it, preventing it from ever reaching the site's servers.
Another approach is to flag suspicious individual machines that seem to be behind an attack, and ban any traffic from them from reaching the site.
That can often be difficult, though, because criminals use "proxy" computers to route their traffic, masking the source of the original requests. Proxy computers are often other infected computers that are part of a botnet.
Q: Is there usually evidence of who the culprits were? Or is the nature of the attack such that it leaves few fingerprints?
A: It's usually easier to stop a denial-of-service attack than it is to figure out who's behind it. Simply identifying where the malicious traffic is coming from won't get investigators very far, since the infected PCs that get roped into a botnet are owned by innocent people who don't know their computers are being used for nefarious purposes.
Pat Peterson, a security researcher and fellow at Cisco Systems Inc., says sophisticated attackers have also been adding a more subtle approach to evade detection.
Instead of directing huge amounts of traffic at a target site, they'll make more complicated requests one at a time that eat up more of the site's computing power, like trying to log in using bogus usernames and passwords. If enough of those requests are made, on a site that requires a lot of computing power, the effect can be the same, and the site gets knocked out.
This type of attack is trickier because it doesn't involve the sort of massive traffic surge that would normally tip off network administrators.
This advanced tactic wasn't necessarily used in the most recent attacks. In fact there are signs the attacks were relatively amateurish. The programming code appears to have been patched together largely from material that has been circulating in the criminal underground for several years, according to Jose Nazario, manager of security research for Arbor Networks.
Q: If these attacks make use of compromised computers corralled into a "botnet," should I be worried about whether my PC is one of them? What could I do to prevent that or fix it?
A: If your computer is being used in a denial-of-service attack, you're likely to see a significant slowdown, because your processing power is being siphoned for the assault. But there aren't always obvious signs that your computer has been infected.
So the best thing is to focus on prevention, namely by having up-to-date antivirus software. In particular, make sure your antivirus software gets updated over the next few days.
If you're concerned your machine might be infected, it's wise to run an antivirus scan. Many antivirus companies offer a free scan from their Web sites.
Placemaker by Yahoo - location awareness
What is Placemaker?
Placemaker provides developers with the means to geo-enrich their content, such as web pages, blog posts, feeds, news articles, status updates, and their applications which make use of such information. Placemaker is an open API; it helps developers to make applications and data sets location aware. Placemaker is not a geocoder, it is a geo-enrichment service that assists in determining the whereness of unstructured content and helps make the Internet increasingly hyper local.
How does Placemaker Work?
1. Developers specify structured and unstructured content; feeds, web pages, news, status articles, etc.
2. Placemaker identifies, disambiguates and extracts places
3. Placemaker returns geographic metadata, which determines thewhereness of structured and unstructured content
How do I access Placemaker?
Just as for Yahoo! GeoPlanet, accessing Placemaker is simple:
1. Read the online documentation and user guide atdeveloper.yahoo.com/geo/placemaker/guide
2. Get an Application Id at developer.yahoo.com/wsregapp
3. POST your content towherein.yahooapis.com/v1/document supplying your Application Id.
Is using Placemaker Free?
Yes, Placemaker is an open and freely available geo-enrichment tool; you need to have a valid Application Id but there is currently no formal rate limiting imposed. In the future, we may permit commercial usage with partners under separate terms but we want to ensure that the service remains free, open and available.
Where Does Placemaker Fit in With Yahoo! Geo Technologies’ products?
The Yahoo! Geo Technologies group wants to connect our users with the world around them. Yahoo! is an information and technology company – we collect and create content, and get it into the hands of our users in the most relevant and useful way possible. Geography plays a big part in how we do that; we are always looking at how we can better join the Web world and the real world.
Last May, we released Yahoo! GeoPlanet, which helps bridge the gap between the real and virtual worlds by providing an open, permanent, and intelligent infrastructure for geo-referencing data on the Internet. You can learn more athttp://developer.yahoo.com/geo/.
In the fall, we introduced Fire Eagle, which acts as a location broker that allows users to take their location to the Web. Users have complete control over their data with Fire Eagle: they choose which third-party applications to share their location with, and at what resolution or granularity they wish to expose it –- as broad as country or state, to as detailed as a long/lat coordinate, and everything in between. More information is athttp://fireeagle.yahoo.net/.
Now, with Placemaker, we can help developers and publishers make applications and data sets location-aware by determining thewhereness of unstructured content. Once users share their location information using FireEagle, we help provide hyper-local information based on their geography, adding value to content that is delivered to them wherever they are.
The bottom line is that location-aware systems provide a more topical, more relevant user experience. When users interact with the Internet and, more specifically, with Yahoo!, we aim to provide them with the most geo-relevant information available.
Placemaker and Privacy
Privacy on the Internet is an important issue and one which Yahoo! Geo Technologies takes very seriously. There are no privacy concerns or issues with Placemaker; the web service acts on content which is already available on the Web, it does not act on a user’s location.
How do I Find out More?
If you visited the Yahoo! booth at Where 2.0 you may have seen our Placemaker handout, but if you’ve lost this or weren’t lucky enough to be at Where 2.0 you can download a PDF copy of it here. Other Geo Technologies and Placemaker resources include:
- Placemaker – developer.yahoo.com/geo/placemaker
- Placemaker Guide –developer.yahoo.com/geo/placemaker/guide
- Placemaker Forum – developer.yahoo.net/forum/index.php?showforum=98
Yahoo Query Language for developers who enjoys webservice
What is YQL?
The Yahoo! Query Language is an expressive SQL-like language that lets you query, filter, and join data across Web services. With YQL, apps run faster with fewer lines of code and a smaller network footprint.
Yahoo! and other websites across the Internet make much of their structured data available to developers, primarily through Web services. To access and query these services, developers traditionally endure the pain of locating the right URLs and documentation to access and query each Web service.
With YQL, developers can access and shape data across the Internet through one simple language, eliminating the need to learn how to call different APIs.
How Do I Get Started?
- Check out the YQL Console.
- Read how to access YQL from your application.
- Get your API Keys to sign your requests if you need them.
Using the API or Web Service
YQL Overview
YQL exposes an SQL-like SELECT syntax that is both familiar to developers and expressive enough for getting the right data. Through the SHOW and DESC commands, we enable developers to discover the available data sources and structure without opening another Web browser.
YQL Open Data Tables
Open Data Tables enable developers to add tables for any data on the Web to our stable of API-specific tables. Using Open Data Tables, anyone can make their data YQL-accessible. If you would like to create an Open Data Table, visit the community page at http://datatables.org.
Examples:
YQL Execute
Building upon Open Data Tables, the Execute element gives developers full control of how the data is fetched into YQL and how it's presented back to the user. With Execute, developers can build tables that manipulate, change, and sign the URLs to access almost any protected content. This lets YQL access and combine data across a variety of different authenticated services such as Netflix or Twitter. Developers can call multiple services and data sources within Execute to join and mash up data however they desire, letting Yahoo! do the work rather than their applications. Data can be tweaked and manipulated into an optimal format for applications to consume.
Execute elements run server-side JavaScript with E4X (native XML) support. This gives developers a fully functional language that Web developers know, and lets them do almost anything they want with the data. We've added a few new global objects to the language to enable developers to: include JavaScript libraries and code from any URL; fetch data from any URL/Web page; run other YQL commands; and perform data filtering and conversion.
Examples:
CSS selectors for HTML - a CSS selector table for getting data from HTML pages
use "http://yqlblog.net/samples/data.html.cssselect.xml";
select * from data.html.cssselect;Unified web+image search - perform a BOSS search that also returns an image from the BOSS image search for the same site and query term in a single result set
use 'http://yqlblog.net/samples/search.imageweb.xml' as searchimageweb;
select * from searchimageweb where query='pizza'YQL Insert/ Update/ Delete
You can use YQL to write and modify data on Web services and applications using SQL keywords: INSERT, UPDATE, and DELETE. These verbs let you manipulate data mapped onto an Open Data Table and enables developers to use Open Data Tables to do the following:
- insert new Twitter status messages, not just list them
- add new comments to a blog, as well as read them
- store data in a remote database
- INSERT INTO Internet
Open Data Table (ODT) developers can add support for these verbs into their tables by creating new binding types in their ODT definitions. They can then perform the insert/update/delete on the remote web service by creating an execute element that runs their JavaScript to create the right content payload and send it to the remote service. We've extended the capabilities in our server-side JavaScript, so y.rest() can now POST, PUT and DELETE.
Try creating a new tweet from the YQL console by following this link:
use 'http://www.yqlblog.net/samples/twitter.status.xml'; insert into twitter.status (status,username,password) values ("Playing with INSERT, UPDATE and DELETE in YQL", "twitterusername","twitterpassword")
Usage limits
YQL has the following API usage restrictions:
Per application limit (identified by your Access Key):
- 100,000 calls per day.
Per IP limits:
- /v1/public/* 1000 calls per hour
- /v1/yql/* 10000 calls per hour
All rates are subject to change. In addition, you may also be subject to the underlying rate limits of other Yahoo and 3rd party web services.
Please contact yql-questions [at] yahoo-inc.com with requests for additional limits and information.
Chrome OS by Google - Can it bury microsft's windows?
Google is developing an open-source operating system targeted at Internet-centric computers such as netbooks and will release it later this year, the company said Wednesday.
The OS, which will carry the same "Chrome" name as the company's browser, is expected to begin appearing on netbook computers in the second half of 2010, Google said in a blog post.
It is already talking to "multiple" companies about the project, it added.
The Chrome OS will be available for computers based on the x86 architecture, which is used by Intel and Advanced Micro Devices(AMD), and the Arm architecture.
Prototypes of Arm-based netbooks began appearing last month at the Computex show in Taiwan and Google's support for the architecture could give it a significant boost. Microsoft's mainstreamWindows operating system doesn't run on Arm chips so many manufacturers were talking about using Linux or a version of Google's Android operating system. It's not immediately clear how much the two operating systems share in common code but Google said they are aimed at very different devices.
"Google Chrome OS is a new project, separate from Android," it said. "Android was designed from the beginning to work across a variety of devices from phones to set-top boxes to netbooks. Google Chrome OS is being created for people who spend most of their time on the Web."
While Google is initially looking at the netbook segment of the market it might compete with Microsoft and Apple on larger, Internet-centric machines.
Chrome OS is "being designed to power computers ranging from small netbooks to full-size desktop systems," said Google.